Are you primed and ready for beta testing?
When it comes to the environment, tools, participants, and other important aspects, you’ve already covered all the bases.
But have you given proper attention to security and privacy?
As one of the most important factors for successful beta testing, security and privacy measures shield the beta version of your app from curious competitors and safeguard against leaks to the wider public.
That’s precisely why, in this article, we’ll dive into intricate details surrounding the privacy and security concerns that accompany beta testing.
Not only that, we’ll arm you with best practices that will enable you to tackle these challenges head-on.
Stay tuned for tips and tricks of the trade!
Table of Contents
Take extra security measures
During the beta testing phase, it’s not uncommon to encounter security incidents that throw a wrench into the testing process and leak new features to lurking competitors.
To illustrate this point, let’s delve into the gaming world and examine the case of Call of Duty: Modern Warfare 2.
The launch of the beta phase of a highly anticipated multiplayer game such as this one is bound to grab the attention of not only eager fans but also hackers seeking vulnerabilities to exploit.
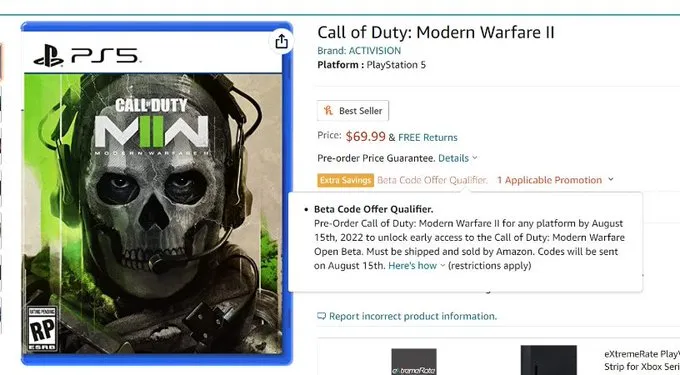
And that’s precisely what went down in 2022 when mischievous hackers decided to meddle with the testers, causing disruptions even before the curtain rose.
Infinity Ward, the company responsible for developing the game, swiftly sprang into action to combat these hackers, as evidenced by their tweet below.
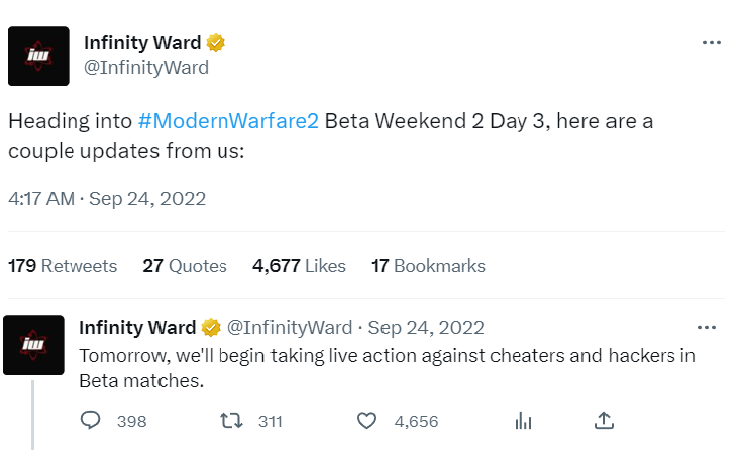
When such incidents befall a prominent brand, the repercussions are twofold: the negative publicity can reverberate for months, while simultaneously posing a significant threat to security and confidentiality.
It’s, therefore, crucial to fortify your app against data leaks, security attacks, intellectual property theft, and other detrimental occurrences that can put its reputation, sensitive data, and trade secrets in jeopardy.
Hackers also have the potential to breach your app’s system and security, pilfering credentials, API keys, proprietary information, and more.

Get unreal data to fix real issues in your app & web.
The cumulative impact of these breaches can inflict substantial damage on a company’s bottom line.
The smart approach to combating this is to employ application hardening. Just as the name implies, this process aims to make your app a tough nut to crack.
Application hardening relies on several powerful techniques, including:
- Obfuscation: a method of obscuring the code to make it difficult for attackers to conduct reverse engineering, where the app is deconstructed in order to understand it and build a copy of it
- White-box cryptography: an approach that combines encryption and obfuscation to embed secret keys in the code
- Authentication hardening: a process of securing the login and authentication processes
While we have only highlighted a few renowned techniques on this list, there are numerous others at your disposal.
Bear in mind that application hardening isn’t a one-time event but an ongoing process.
To ensure optimal protection for your application, you must consistently upgrade and refine your security measures.
Disclose which app permissions are needed
In a Google research study, an intriguing finding emerged: 15% of participants hit the uninstall button on an app because it requested permissions they didn’t understand or which they simply regarded as unnecessary.
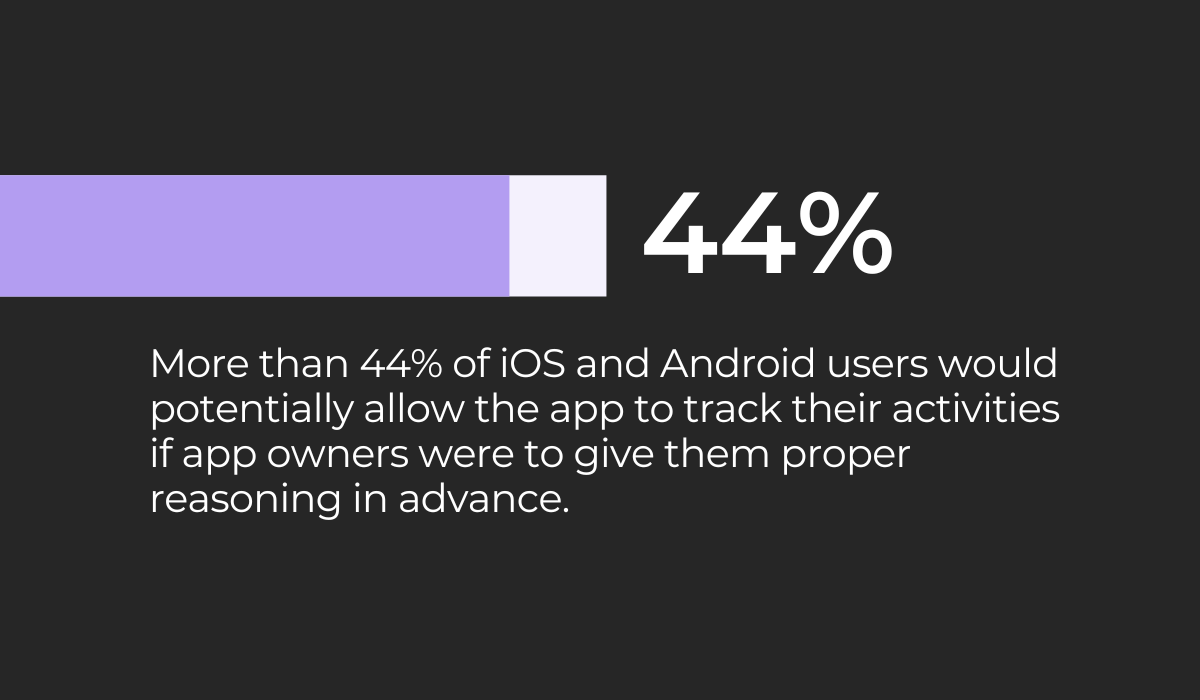
Meanwhile, a Pollfish study revealed that over 44% of iOS and Android users would permit an application to track their activities if they received clear and compelling reasoning in advance.
These numbers speak volumes about how users feel about the app collecting data they weren’t informed of beforehand, and this rings true for beta testers as well.
When beta testers don’t fully grasp the app’s permission requests, their concerns about privacy may trigger a decision to withdraw from the testing process.
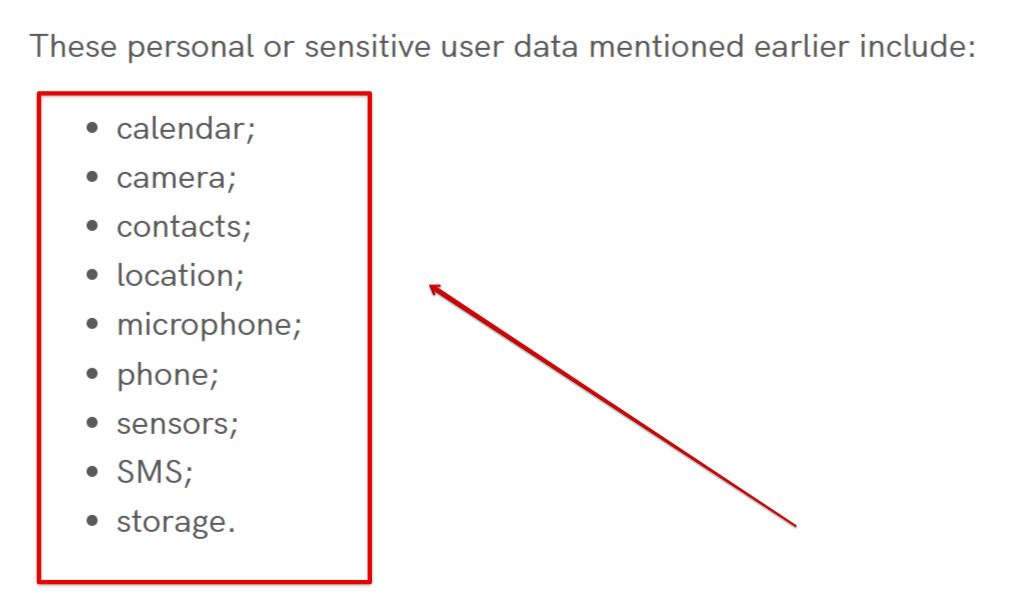
Therefore, whenever you need to use the personal or sensitive data of beta testers, you’ll need to have an in-app disclosure policy that leaves no stone unturned in explaining how you conduct privacy practices.
The image below showcases the various scenarios this policy can encompass.
To further highlight the importance of this issue, let’s examine the infamous Roomba beta testing fiasco.
Between 2019 and 2022, beta testers were granted Roomba vacuum cleaners to use in their homes.
In return, they consented to the device capturing images and videos and collecting data that would be used to improve their artificial intelligence capabilities.
However, the gravity of the situation became apparent when leaked photos from beta testers surfaced on social media.
To make matters worse, some of these photos featured minors or individuals caught in private moments on the toilet.
The revelation left beta testers feeling betrayed and deceived, as they believed they hadn’t provided consent for such invasions of their privacy.
Albert Fox Cahn, the Surveillance Technology Oversight Project executive director, explained it this way:
There is a real concern about whether the company is being deceptive if people are signing up for this sort of highly invasive type of surveillance and never fully understand … what they’re agreeing to.
When you don’t have a thorough in-app disclosure policy that clearly informs all testers how you collect, use, and share beta testers’ data, you risk a backlash and a damaged reputation.
It’s important that the policy be located within the tested application itself and not require beta testers to meander through different menus to access it.
In other words, you cannot simply include it in the privacy policy or terms of service and consider your job done.
If you truly want your beta testers to agree to testing, you must be honest and enable them to know precisely what they are getting into in terms of how you use their data.
Choose your beta testers carefully
When it comes to beta testing, one thing can’t be underestimated–the significance of handpicking the right candidates to partake in this process.
It’s not merely about collecting data about your application and its pesky bugs and other bottlenecks.
It’s also about ensuring that no confidential information falls into the hands of your competitors or the prying eyes of the general public.
In simpler terms, you need beta testers who can keep their lips sealed.
Let’s look at a couple of real-life examples to truly grasp the weight of this issue.
In the first example, sourced from Reddit, a beta tester thoughtlessly shared footage of a popular game with a friend, who subsequently published it on the internet.
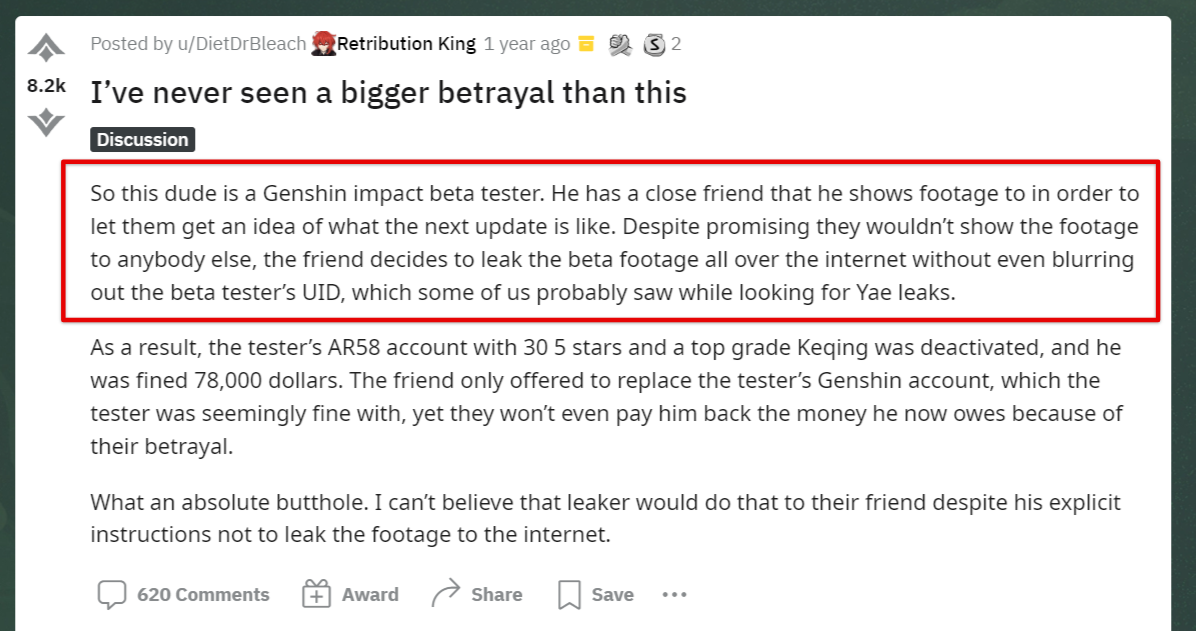
The beta tester was punished by losing its account and receiving a hefty financial penalty.
But the damage was also done to the game itself because critical features, still undergoing beta testing, were exposed prematurely.
In the second example, a Tesla employee and a beta tester for Full Self-Driving (BSD) features posted on his popular YouTube channel not only footage of the BSD in action but also its navigational limitations and quite a dramatic moment when he crashed into a traffic bollard.
Although the latter example doesn’t concern mobile apps, it’s a clear indication of what could happen if the beta version of your product gets into the wrong hands.
That’s why, during the candidate selection process, it becomes paramount to create an application form that will survey beta testers for crucial information while also revealing potential red flags.
Let’s illustrate this point with Recolor’s beta test application form.
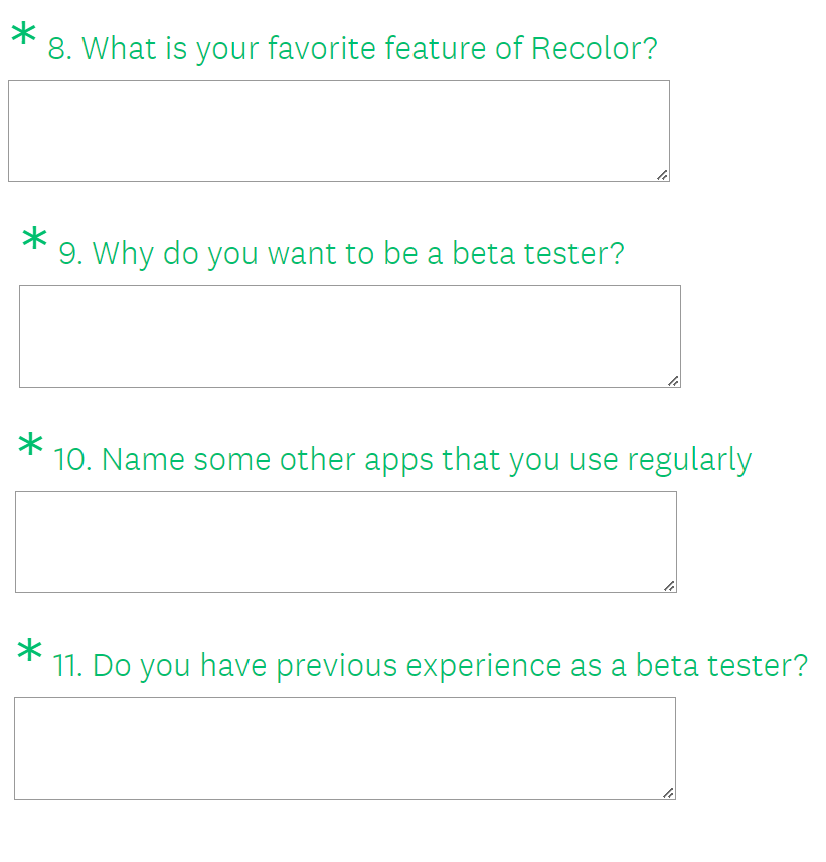
Recolor, a well-known application that offers coloring books for adults as a means of alleviating stress, first asks potential beta testers standard questions such as their name, surname, and age.
Then, as you can see in the image below, it requires them to articulate their favorite Recolor feature, explain why they want to be beta testers, and share any previous experience in the field.
Based on these answers, the individuals responsible for the application process can better assess whether someone is suitable for the beta testing, and detect warning signals if someone might misuse the testing.
Another thing you can do during the testing process is to consistently remind testers about the confidentiality of the data.
Even seemingly insignificant things like marking documents as confidential or emphasizing the importance of data secrecy can deter them from accidentally leaking information publicly.
If you prioritize data confidentiality, everyone involved in the process will take it seriously.
Have testers sign a Beta test agreement
When planning beta testing, one of the most common mistakes you can make is not considering the legal aspect.
The fact that the application is still in the beta testing phase doesn’t automatically mean that you should disregard legalities and put them on the back burner.
In fact, it’s wise to create a comprehensive Beta test agreement, as it brings a host of perks, some of which are as follows:
- Agreement on terms and conditions–by implementing a Beta test agreement, you allow all beta testers to carefully review and consent to the testing’s terms and conditions before they can participate
- Addressing privacy concerns–the agreement guarantees that all beta testers are fully informed about their privacy concerns and the expectations they should have from the program itself
- Safeguarding intellectual property–the agreement also functions as a legal document protecting your company’s intellectual property and provides you with recourse against those who might leak data to third parties
During the beta testing phase, it’s inevitable that your application will encounter bugs and hiccups that you’d prefer to keep under wraps until the official release.
Here’s where the Beta test agreement becomes even more indispensable.
It offers vital legal protection against any misuse of the application during this sensitive phase, as exemplified by the practices of Tesla and other companies.
Curious about what this agreement might look like?
Take a glance at the image below, which provides not only an example of it but can also serve as a template for your own beta-testing endeavors.

The Beta test agreement usually consists of the following items:
- Copyright specifics
- Liability protections
- Non-disclosure agreement (NDA)
- Privacy policy
- Term of service
- The roles and powers of the company and tester
- Dispute resolution process
You may have noticed that the list also includes an NDA, which usually functions as a separate legally binding document that stipulates data confidentiality.
It’s important to note here that while beta agreements differ from NDAs, they often contain short NDAs to further emphasize privacy, confidentiality, and disclosure.
Of course, for the Beta test agreement to be legally binding, all beta testers must sign it before accessing the testing.
Fortunately, there are numerous add-ons and special software available on the market, especially for this purpose.
Remember, the beta testing agreement is one of the most important documents that protects and regulates both you and the beta testers and you should, therefore, prioritize its creation.

Don’t disregard the risk of piracy
While your application is in the beta phase, meaning it’s in the last testing phase before the launch, you have already come a long way from the idea to development.
The last thing you want is for all your efforts to go to waste because someone hijacks the beta testing process and pirates your app.
The threat of piracy is real and can have significant consequences for your app–it can give your competitors a heads-up or damage the reputation of your brand.
That’s why it’s important to take precautions and adopt certain tactics to reduce the risk of piracy during beta testing.
For starters, you can choose the proper platforms for distributing the beta app to beta testers that provide an additional layer of security.
TestFlight, TestFairy, and Appaloosa are some of those platforms that have specific features that enhance security.
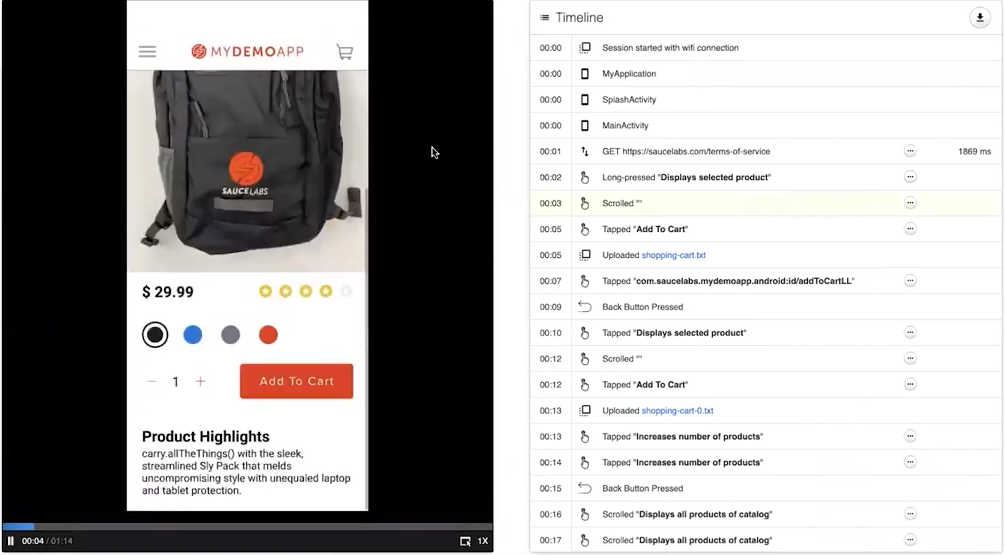
TestFairy, for example, besides being on the cloud, can be hosted on-premise to enhance security, and it can also integrate with Okta and OneLogin, which will allow you to securely connect your beta testers with the beta app through various authentication measures.
Appaloosa, on the other hand, supports SAML, OAuth, and SAML SSO solutions to enhance testing security and prevent hacking.
What will also protect the confidentiality of data is having a Non-Disclosure Agreement (NDA) in place.
Although in its condensed form, an NDA can be part of the Beta test policy (which we already discussed earlier), you can request that your beta testers also sign a separate NDA document, pledging to keep confidential information about your application secret.
Capture, Annotate & Share in Seconds with our Free Chrome Extension!
Chances are, your legal department has already created such a document for your convenience.
However, if you find yourself lacking one, you can easily access numerous top-notch templates on the internet, such as the one from LawDistrict.
Only after the agreement has been inked should beta testers proceed with their testing responsibilities.
Beta testers who aren’t comfortable signing an NDA should be excluded from the beta testing process and denied access.
Conclusion
There you have it–the five most important privacy and security considerations that you need to be aware of when beta testing your app.
This list is by no means exhaustive, but it’s a great starting point for anyone interested in safeguarding the beta version of their app from prying eyes.
While these measures may have drawbacks and won’t necessarily protect you from every threat out there, they’ll minimize the impact of any potential damage.